Theresa May has failed to deliver Brexit, Promised to sign the UN Migration pact and thus continued facilitating the Jihad domination of Europe and her country and is installing a Chinese communist Spy grid throughout Western Europe's infrastructure.
***Article first published by 'Zero Hedge' on April 30, 2019***
As Huawei denies Microsoft's allegations that it discovered what appears to be a 'backdoor' built into the Matebook laptop series, Bloomberg on Tuesday reported on complaints from Vodafone, Europe's largest wireless provider, about the discovery of what appear to be 'backdoors' discovered in Huawei equipment embedded in Vodafone's Italian wireless network, potentially going back years.
Though Huawei has tried to cast these complaints, detailed in a series of emails obtained by Bloomberg, as innocuous glitches, but Vodafone's acknowledgement of these concerns appears to support Washington's warnings that Huawei equipment represents an international security risk - though the European Council and most individual states have done little to prevent Huawei equipment from being used in the Continent's 5G wireless networks.
The vulnerabilities identified by Vodafone could grant Huawei access to the 'fixed-line network' in Italy, the system that provides Internet service to millions of homes and businesses, potentially exposing a large swath of the Italian population to spying by the Chinese.
After Vodafone approached Huawei in 2011 with its complaints, the Chinese telecoms giant offered assurances that the issues had been fixed; however, further testing revealed that Huawei had mislead Vodafone. What's more, Vodafone also identified backdoors in its fiber-optic network, potentially exposing Internet traffic in Italy to Chinese spying.
Despite all of this, Vodafone did nothing after discovering backdoors throughout its Italian network and even catching Huawei in a lie when the company said it had fixed the issues, but Vodafone discovered that it hadn't.
These concerns didn't stop Vodafone for increasing its reliance on Huawei's equipment, which underscores why European governments have been so reluctant to heed Washington's warnings: Huawei is simply too important to Europe's telecoms infrastructure. Spurning Huawei would put Europe at risk of falling behind the US and China in the race to build out 5G infrastructure.
Vodafone CEO Nick Read has joined peers in publicly opposing any restrictions on Huawei equipment in Vodafone's 5G networks.
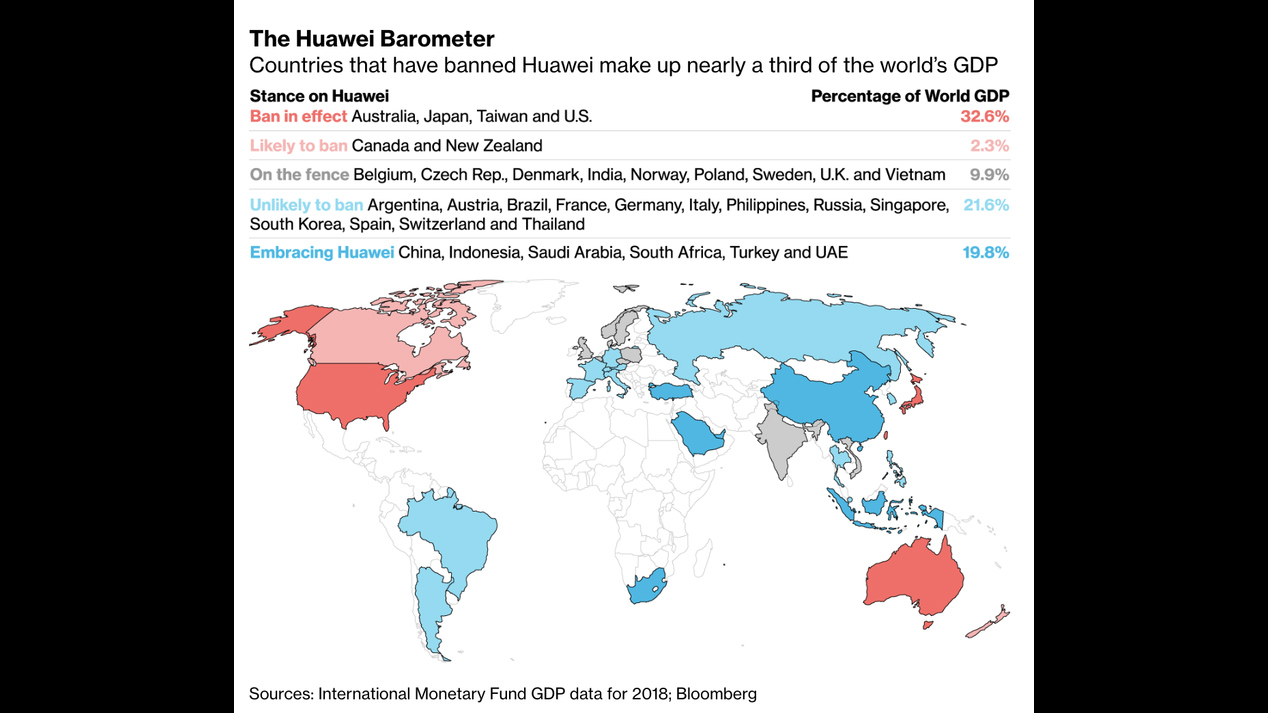
Most European countries are unlikely to crack down on Huawei over these security concerns.
And clearly, the issue didn't sour the Italians on China, since Italy recently became the first G-7 country to join Beijing's "Belt & Road Initiative", which has been derided by critics as a "neocolonialist project."
In addition to the security concerns in the core Italian network, Vodafone also complained about suspected vulnerabilities in routers shipped by the company. But both Huawei and Vodafone cautioned that these could have been the result of an unintentional flaw.
In a statement to Bloomberg, Vodafone said it found vulnerabilities with the routers in Italy in 2011 and worked with Huawei to resolve the issues that year. There was no evidence of any data being compromised, it said. The carrier also identified vulnerabilities with the Huawei-supplied broadband network gateways in Italy in 2012 and said those were resolved the same year. Vodafone also said it found records that showed vulnerabilities in several Huawei products related to optical service nodes. It didn’t provide specific dates and said the issues were resolved. It said it couldn't find evidence of historical vulnerabilities in routers or broadband network gateways beyond Italy.
"In the telecoms industry it is not uncommon for vulnerabilities in equipment from suppliers to be identified by operators and other third parties," the company said. "Vodafone takes security extremely seriously and that is why we independently test the equipment we deploy to detect whether any such vulnerabilities exist. If a vulnerability exists, Vodafone works with that supplier to resolve it quickly."
In a statement, Huawei said it was made aware of historical vulnerabilities in 2011 and 2012 and they were addressed at the time.
But some of BBG's other sources warned that backdoors were discovered in networks across Europe, and that Vodafone had sought to play down these discoveries.
However, Vodafone’s account of the issue was contested by people involved in the security discussions between the companies.
Vulnerabilities in both the routers and the fixed access network remained beyond 2012 and were also present in Vodafone’s businesses in the U.K., Germany, Spain and Portugal, said the people. Vodafone stuck with Huawei because the services were competitively priced, they said.
Emails obtained by BBG also revealed that some Vodafone executives were shocked by Huawei's unwillingness to fix the backdoors, and its decision to lie about the issues being fixed.
"Unfortunately for Huawei the political background means that this event will make life even more difficult for them in trying to prove themselves an honest vendor," Vodafone said in the April 2011 document authored by its chief information security officer at the time, Bryan Littlefair. He noted that Vodafone had made a recent security visit to Shenzhen and said he was surprised Huawei hadn’t given the matter a greater priority.
"What is of most concern here is that actions of Huawei in agreeing to remove the code, then trying to hide it, and now refusing to remove it as they need it to remain for ‘quality’ purposes," Littlefair wrote.
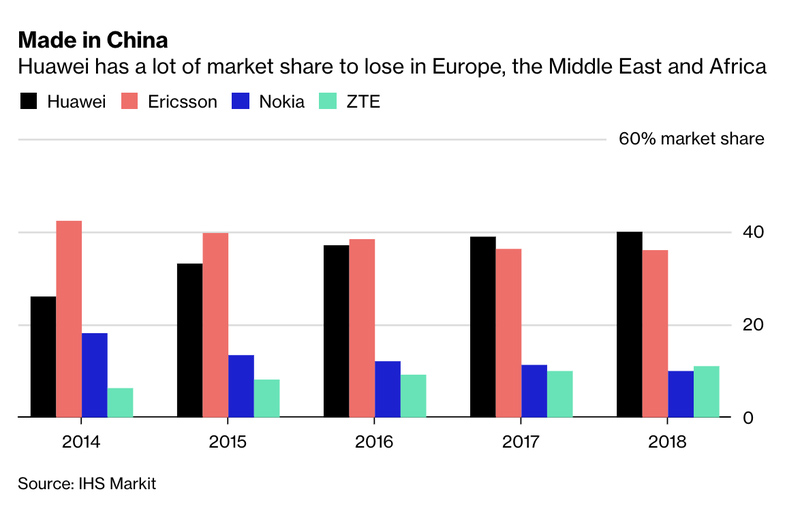
Of course, Huawei has a lot of market share to lose in Europe, and therefore it's incumbent on the firm to keep its customers happy.
But then again, if telecoms companies in Europe continued to use Huawei equipment in such sensitive capacities after this incident, then apparently switching to Ericsson or Nokia technology isn't really an option.